Overview of BBE
There may be situations when an organization needs to tokenize sensitive data in a web form but an iFrame is not the preferred solution. In this scenario, TokenEx provides a JavaScript library that utilizes a TokenEx RSA public encryption key to encrypt sensitive information within the web form. When the form is submitted, the encrypted data will posted to the hosting web server. Because only TokenEx can decrypt the ciphertext, there is less risk of a sensitive data breach in the event the web server is compromised.
Once the ciphertext has been sent to the web server, the encrypted value(s) can be passed to TokenEx via a Web API to be tokenized.
NOTE:
While use of the TokenEx iFrame may qualify an e-commerce merchant accepting only card-not-present transactions to complete a Self-Assessment Questionnaire (SAQ) A, use of Browser Based Encryption (BBE) typically requires completion of an SAQ A-EP.
For more information on the PCI requirements related to e-commerce solutions, see the PCI Security Standards Council "Best Practices for Securing E-commerce" Information Supplement.
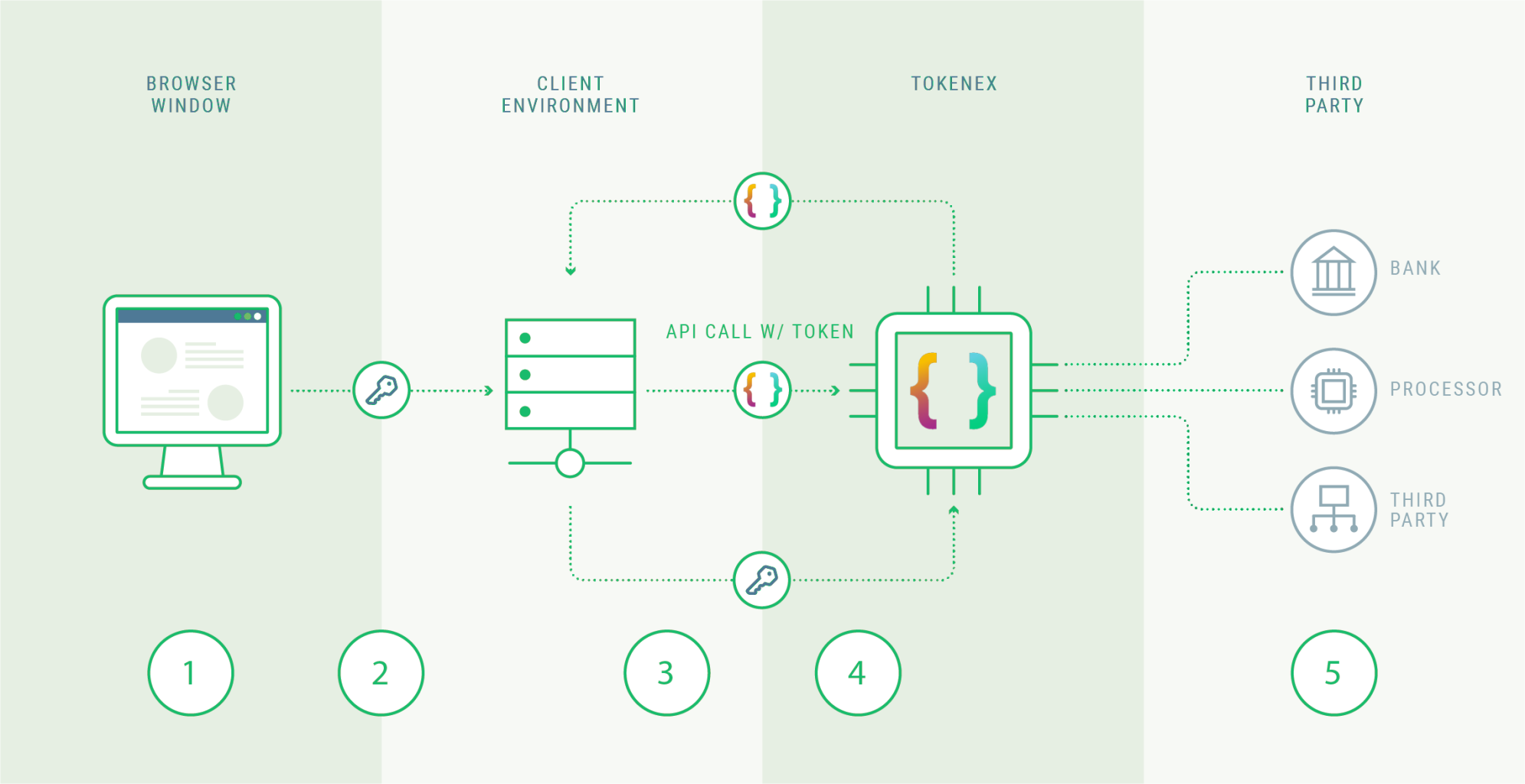
| Step |
|---|
| 1. Sensitive data is encrypted in the customer's web browser using the TokenEx BBE JavaScript library and RSA public encryption key. |
| 2. The non-sensitive and encrypted sensitive data (ciphertext) is submitted to the TokenEx client's web server. |
| 3. The TokenEx client makes a Web API call to TokenEx with the encrypted value(s). TokenEx decrypts and tokenizes the sensitive data. |
| 4. TokenEx returns the token to the client's server. The TokenEx client can then send the tokenized data to a third-party such as a payment gateway, using the Payment Services API or Transparent Gateway API. |
| 5. TokenEx replaces the tokens in the client's API call to a third-party with the corresponding sensitive data. |
Updated 12 months ago
