What is Tokenization?
Tokenization Overview
Tokenization is the process of exchanging sensitive data for non-sensitive data called "tokens" that can be used in a database or internal system without bringing it into scope. Sensitive data could include credit card data, medical information, Social Security numbers, or anything else that requires security and protection.
Although the tokens are unrelated values, they retain certain elements of the original data—commonly length or format—so they can be used for uninterrupted business operations. The original sensitive data is then safely stored outside of the organization's internal systems.
Unlike encrypted data, tokenized data is undecipherable and irreversible. This distinction is particularly important: Because there is no mathematical relationship between the token and its original number, tokens cannot be returned to their original form without the presence of additional, separately stored data.
A breach of a tokenized environment will not compromise the original sensitive data.
What are the benefits of Tokenization?
The goal of an effective tokenization platform is to remove any original sensitive payment or personal data from your business systems, replace each data set with an undecipherable token, and store the original data in a secure cloud environment that’s separate from your business systems.
For example, tokenization in banking protects cardholder data. When you process a payment using the token stored in your systems, only the original credit card tokenization system can swap the token with the corresponding primary account number (PAN) and send it to the payment processor for authorization. Your systems never record, transmit, or store the PAN—only the token.
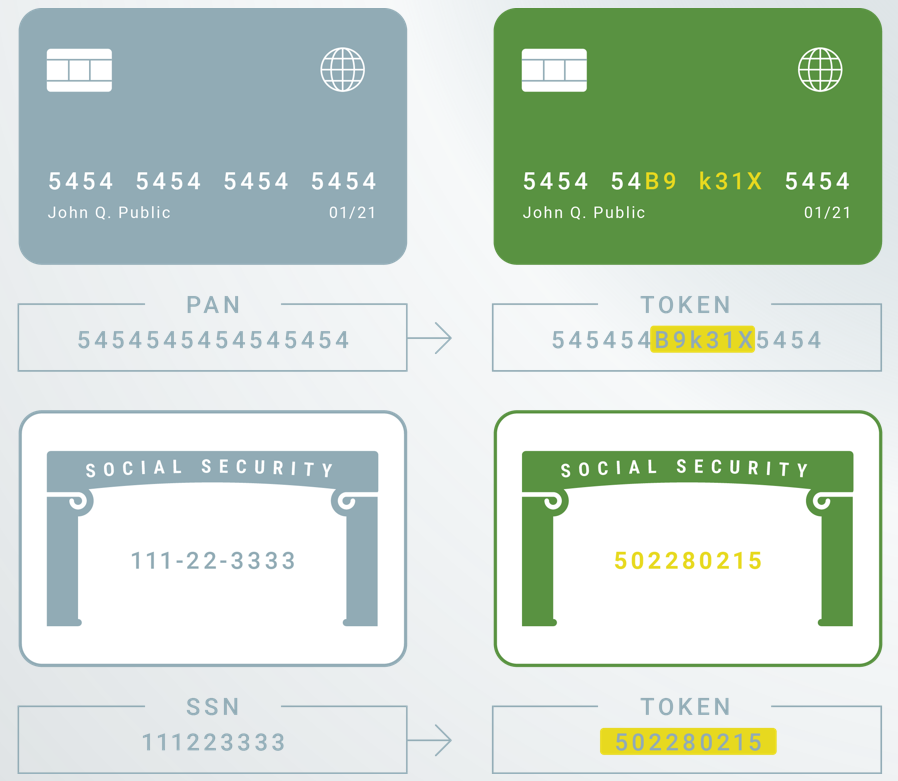
Tokenization Examples
Although no technology can guarantee the prevention of a data breach, a properly built and implemented cloud tokenization platform can prevent the exposure of sensitive data, stopping attackers from capturing any type of usable information—financial or personal.
The advantage to cloud tokenization is there is no information available to steal when the inevitable breach happens. Because of this, it virtually eliminates the risk of data theft.
Additional Resources
Do you have additional questions about Tokenization? Feel free to contact us.
Updated over 1 year ago
